Creating and viewing access tokens
Table of contents
You can create and view access tokens from the website and command line interface (CLI).
Creating access tokens
Creating legacy tokens on the website
Note: For greater security, we recommend using granular access tokens instead of legacy read-only tokens or legacy automation tokens.
-
In the upper right corner of the page, click your profile picture, then click Access Tokens.
-
Click Generate New Token, then select legacy token from the dropdown menu.
-
(Optional) Name your token.
-
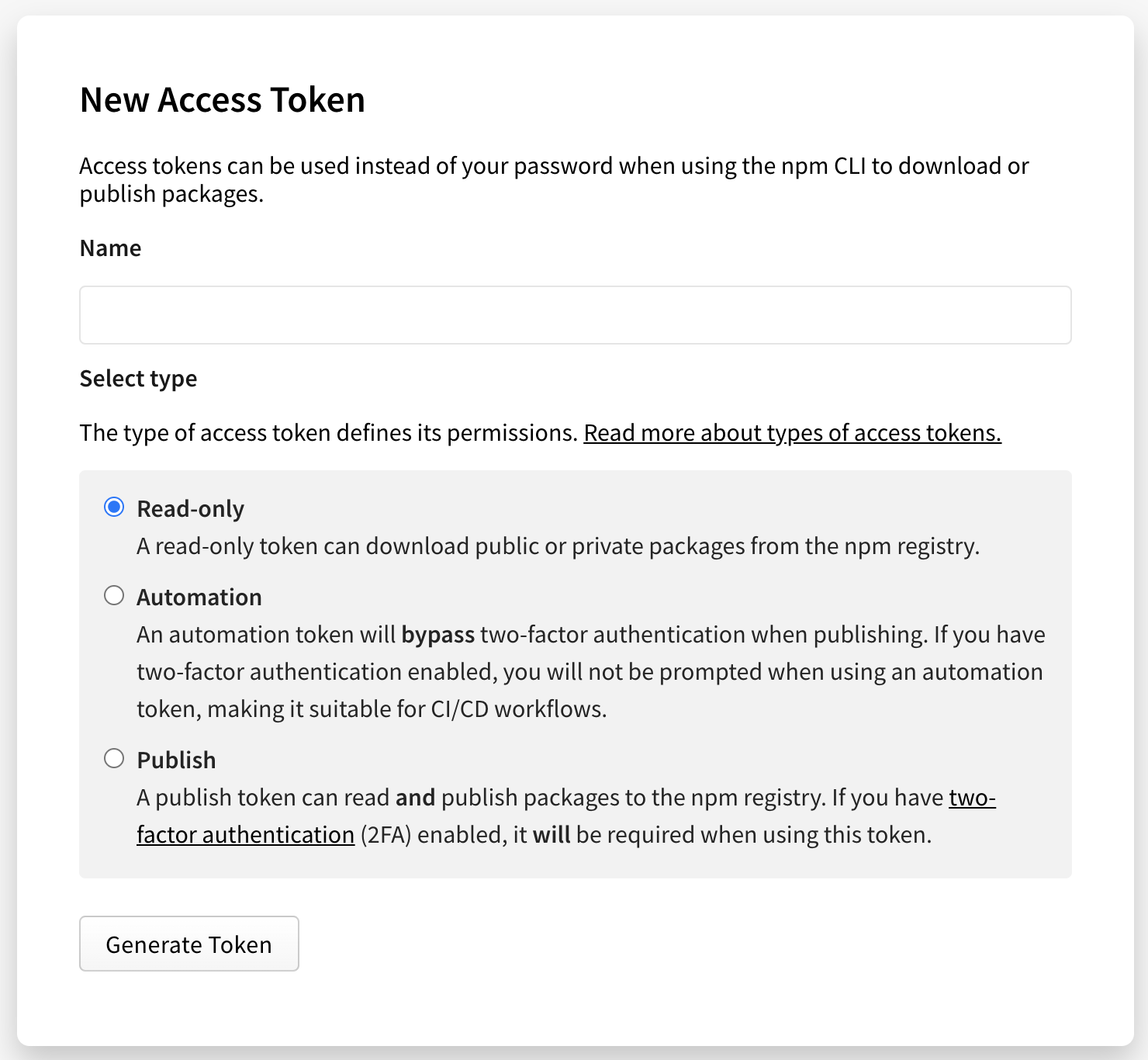
Select the type of access token:
-
Read-only: A read-only token can only be used to download packages from the registry. It will have permission to read any private package that you have access to. This is recommended for automation and workflows where you are installing packages, but not publishing new ones.
-
Automation: An automation token can download packages and publish new ones, but if you have two-factor authentication (2FA) configured on your account, it will not be enforced. You can use an automation token in continuous integration workflows and other automation systems to publish a package even when you cannot enter a one-time passcode.
-
Publish: A publish token can perform any action on your behalf, including downloading packages, publishing packages, and changing user settings or package settings. If you have two-factor authentication configured on your account, you will be required to enter a one-time passcode when using a publish token. This is recommended for interactive workflows such as a CLI.
-
-
Click Generate Token.
-
Copy the token from the top of page.
Creating granular access tokens on the website
-
In the upper right corner of the page, click your profile picture, then click Access Tokens.

-
Click Generate New Token, then click Granular Access Token.

-
In the Token name field, enter a name for your token.
-
(Optional) In the Description field, enter a description for your token.
-
In the Expiration field, enter a token expiration period. The date must be at least 1 day in the future.
-
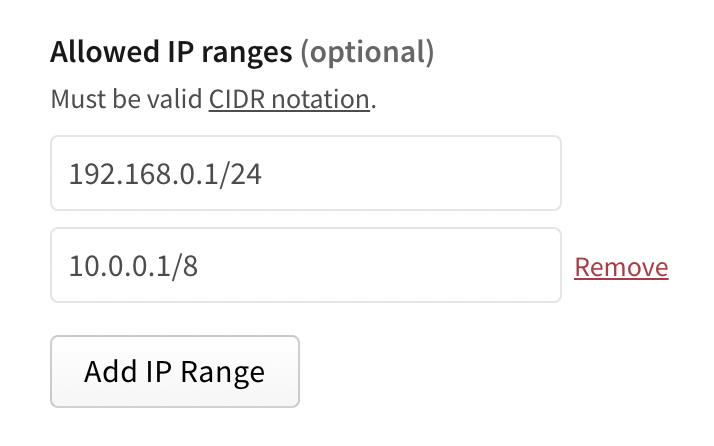
(Optional) In the Allowed IP Ranges field, enter IP address ranges to restrict your access token to. You must use CIDR notation to enter IP address ranges. To add more than one allowed IP range, click Add IP Range and enter an IP range in the new text field.
-
(Optional) In the Packages and scopes section, configure your token's access to packages and scopes.
- In the Permissions dropdown menu, select No access, Read-only, or Read and write.
- Under Select Packages, select either:
- All Packages to grant the token access to all packages the user account has access to.
- Only select packages and scopes to choose up to 50 specific packages or scopes to give the token access to. Then select specific packages or scopes from the dropdown menu.
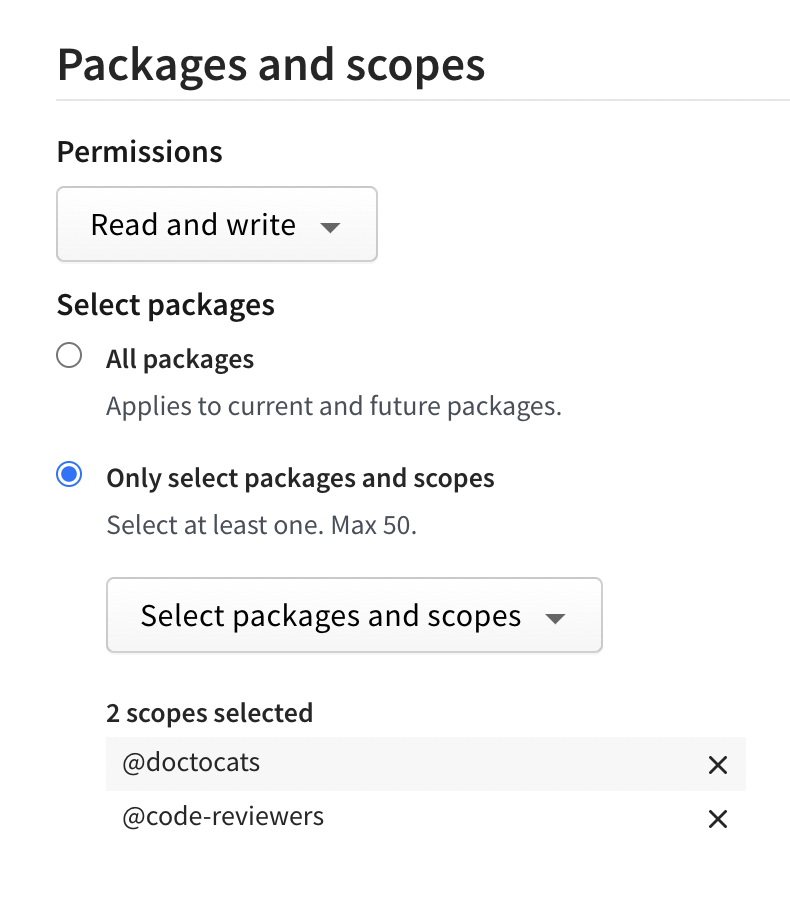
-
(Optional) In the Organizations section, configure your token's access to organizations.
- In the Permissions dropdown menu, select No access, Read-only, or Read and write.
- Under Select organizations, select the organizations you want to grant your token access to.
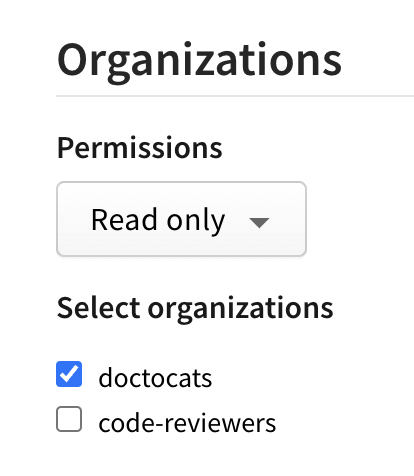
Note: When you give a token access to an organization, the token can only be used for managing organization settings and teams or users associated with the organization. It does not give the token the right to publish packages managed by the organization.
-
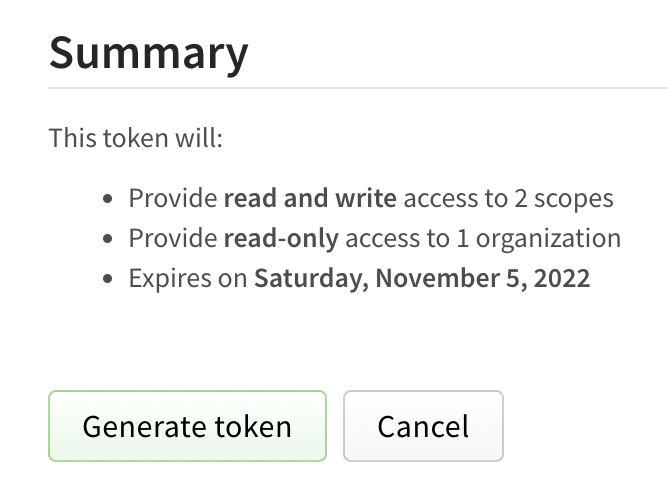
Review the token summary, then click Generate Token.
-
Copy the token from the top of page.
Creating tokens with the CLI
You can create tokens with read-only permissions or read and publish permissions with the CLI.
Note: You cannot create legacy automation tokens or granular access tokens from the CLI. You must use the website to generate these types of tokens. For more information, see "Creating legacy tokens on the website" and "Creating granular access tokens on the website."
- Read-only: Tokens that allow installation and distribution only, but no publishing or other rights associated with your account.
- Publish: The default setting for new tokens, and most permissive token type. Publish tokens allow installation, distribution, modification, publishing, and all rights that you have on your account.
In addition, you can specify that the token is only valid for a specific IPv4 address range, using CIDR notation. The token will only be valid when used from the specified IP addresses.
- To create a new token, on the command line, run:
npm token createfor a read and publish tokennpm token create --read-onlyfor a read-only tokennpm token create --cidr=[list]for a CIDR-restricted read and publish token. For example,npm token create --cidr=192.0.2.0/24npm token create --read-only --cidr=[list]for a CIDR-restricted read-only token
- When prompted, enter your password.
- If you have enabled two-factor authentication, when prompted, enter a one-time password.
- Copy the token from the token field in the command output.
CIDR-restricted token errors
If the CIDR string you enter is invalid or in an inappropriate format, you will get an error similar to the one below:
npm ERR! CIDR whitelist contains invalid CIDR entry: X.X.X.X./YY,Z.Z.. . .
Make sure you are using a valid IPv4 range and try creating the token again.
Viewing access tokens
Note: Full tokens are never displayed, only the first and last four characters will be shown. You can only view a full token immediately after creation.
Viewing tokens on the website
To view all tokens associated with your account, in the upper right corner of the page, click your profile picture, then click Access Tokens.

Viewing tokens on the CLI
To view all tokens associated with your account, on the command line, run the following command:
npm token list
Token attributes
- id: Use the token ID to refer to the token in commands.
- token: The first digits of the actual token.
- create: Date the token was created.
- readonly: If yes, indicates a read-only token. If no, indicates a token with both read and publish permissions.
- CIDR whitelist: Restricts token use by IP address.